|
Token Bucket and Leaky Bucket algorithms are two of the methods used often in managing the network traffic and system design in the transit of data packets over the network. The two algorithms help in the provision of traffic and control of congestion although in different manners. This article explains these algorithms in detail, compares them, and shows the best circumstances under which they should be used.
 Token Bucket vs. Leaky Bucket Algorithm
Important Topics for Token Bucket vs. Leaky Bucket Algorithm
What is the Token Bucket Algorithm?
The Token Bucket Algorithm is a network traffic management mechanism used to control the amount of data that can be sent over a network. It allows for burst traffic while ensuring that the average data transmission rate does not exceed a specified limit. Here’s how it works:
How Does It Work?
- Token Generation: Tokens are generated at a fixed rate and added to the bucket until it reaches its maximum capacity.
- Data Transmission: To send data, tokens are required. For each unit of data to be sent, an equivalent number of tokens is removed from the bucket.
- Burstiness: If the bucket has accumulated tokens (when data transmission was low or idle), a burst of data can be sent all at once as long as there are enough tokens.
- Rate Limiting: If the bucket is empty (no tokens available), data transmission must wait until more tokens are generated, ensuring that the average transmission rate is regulated.
What is the Leaky Bucket Algorithm?
The Leaky Bucket Algorithm is a network traffic management mechanism used to control the rate at which data packets are transmitted over a network. It is designed to smooth out bursts of traffic and ensure a steady, predictable data flow. Here’s how it works:
How Does It Work?
- Incoming Data: Data packets arrive and are added to the bucket.
- Leak Process: Packets are removed from the bucket at a constant rate, simulating a leaking bucket. This rate is predefined and does not change.
- Overflow Handling: If the incoming data rate exceeds the leak rate and the bucket becomes full, any additional incoming packets are discarded (lost), simulating an overflow.
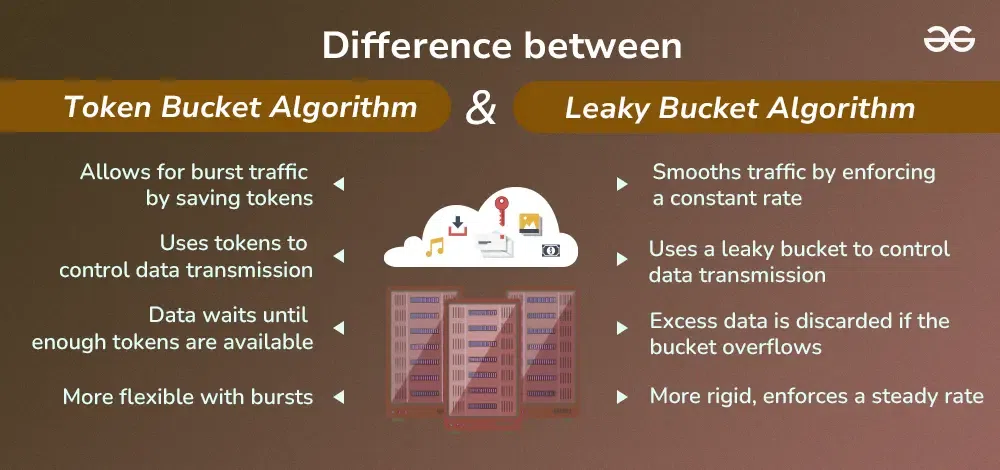
Differences Between Token Bucket and Leaky Bucket Algorithm
Below are the differences between the token bucket and leaky bucket algorithm:
|
Feature
|
Token Bucket Algorithm
|
Leaky Bucket Algorithm
|
|
Traffic Handling
|
Allows for burst traffic by saving tokens
|
Smooths traffic by enforcing a constant rate
|
|
Token/Bucket Concept
|
Uses tokens to control data transmission
|
Uses a leaky bucket to control data transmission
|
|
Data Dropping
|
Data waits until enough tokens are available
|
Excess data is discarded if the bucket overflows
|
|
Rate Flexibility
|
More flexible with bursts
|
More rigid, enforces a steady rate
|
|
Use Case
|
Suitable for bursty traffic and rate limiting
|
Suitable for steady rate enforcement and shaping
|
|
Implementation Complexity
|
Generally more complex
|
Generally simpler
|
|
Buffering
|
Data can be buffered until tokens are available
|
Limited buffering, excess data is dropped
|
Best Scenarios to Use Token Bucket Algorithm
Here are some of the best scenarios to use the Token Bucket Algorithm:
- Handling Bursty Traffic: Applications that generate traffic in bursts rather than at a constant rate, such as video streaming, file transfers, or large data uploads.
- Quality of Service (QoS): Networks that require different levels of service for different types of traffic, such as VoIP (Voice over IP) vs. standard web traffic.
- Rate Limiting: APIs or web services that need to limit the rate of requests to prevent abuse or overloading of resources.
- Traffic Shaping: Internet Service Providers (ISPs) and enterprise networks that need to shape traffic to ensure fair usage and avoid congestion.
Best Scenarios to Use Leaky Bucket Algorithm
Here are some of the best scenarios to use the Leaky Bucket Algorithm:
- Constant Rate Transmission: Ideal for the use where a fixed and reliable throughput rate needs to be guaranteed.
- Traffic Shaping: Aids in reducing large flows in a cycle to avoid a network from being congested by a large number of flWS.
- Network Congestion Management: Through it, the probability of the congestion in the network is minimized since data transmission is made constant.
Conclusion
Summing up, it is possible to state that the application of the Token Bucket and the Leaky Bucket algorithms is more appropriate depending on the determined requirements for the specific application. Token Bucket algorithm is designed for applications that contain bursty traffic patterns that must be smoothed over the long term while at the same time averaging at the desired rate. While that format is good if one expects variability in data flow when one wants to burst through the net and get the streams, Leaky Bucket algorithm works best when there is a need to have uniform data transmission rate where the traffic bursts must be smoothed down.
|

