|
Edge architecture is a computing paradigm that processes data close to its source. This reduces latency, enhances efficiency, and improves data security by minimizing the need for long-distance data transmission. Unlike traditional cloud computing, edge architecture decentralizes processing tasks. It is particularly beneficial in scenarios requiring real-time data analysis. This article explores edge computing, its architecture, components, benefits, and applications. We’ll also discuss challenges, security considerations, and comparisons with other architectures.
Important Topics to Understand Edge Architecture
Understanding Edge Computing
Edge computing is a distributed computing paradigm that brings computation and data storage closer to the location where it is needed. This proximity to data sources reduces latency, enhances performance, and ensures faster decision-making. Edge computing is especially useful in applications requiring real-time data processing and low-latency responses, such as autonomous vehicles, smart cities, and industrial automation.
- Local Processing: Data is processed locally on edge devices or nearby servers, reducing the need to send data to a centralized cloud.
- Real-Time Analysis: Immediate data analysis is possible, enabling quick responses to changing conditions.
- Reduced Latency: By processing data closer to its source, edge computing minimizes latency, ensuring faster data retrieval and processing.
- Bandwidth Optimization: Decreases the amount of data transmitted over networks, conserving bandwidth and reducing costs.
- Scalability: Easily scales to accommodate numerous devices and vast amounts of data without overloading central servers.
- Enhanced Security: By keeping data local, edge computing reduces the risk of data breaches during transmission, improving overall security.
Overview of Edge Architecture
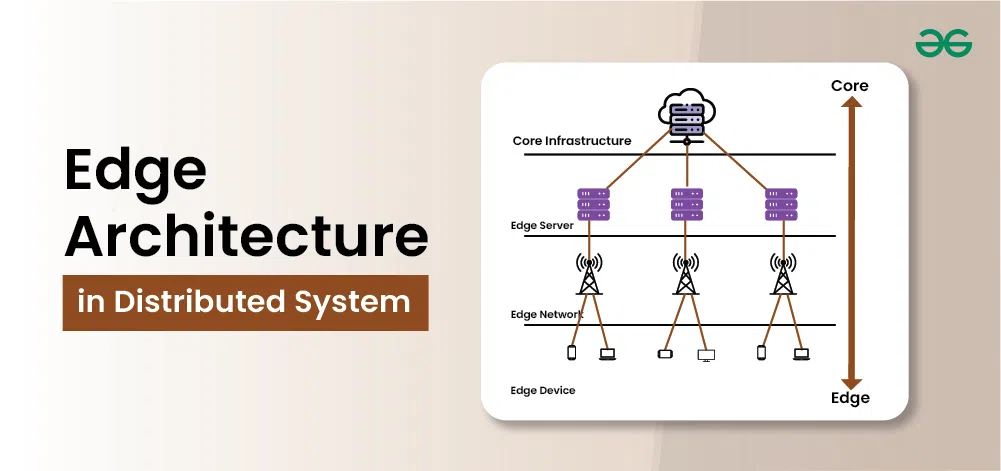
Edge architecture involves distributing data processing tasks closer to where data is generated, rather than relying on centralized cloud servers. This decentralization helps in reducing latency, enhancing real-time data processing capabilities, and improving overall system efficiency. Edge architecture comprises various components, each playing a crucial role in managing and processing data locally.
- Edge Devices: These include IoT devices, sensors, and other hardware that generate data at the edge of the network.
- Edge Nodes: Local processing units that handle initial data processing and analysis before sending relevant information to central servers.
- Edge Servers: Servers located near the edge devices to store and process data locally, reducing the need for data to travel to a distant data center.
- Edge Gateways: Devices that manage data traffic between edge devices and edge servers, ensuring efficient data flow and processing.
- Communication Networks: Networks that connect edge devices, edge nodes, and edge servers, ensuring seamless data transfer and integration.
Key Components and Design Principles
Understanding edge architecture requires knowledge of its key components and design principles. These elements are crucial for implementing efficient and scalable edge computing systems. Here are the requirements to learn these components and principles:
Key Components of Edge Architecture:
- IoT Devices and Sensors: Learn how to work with IoT devices and sensors that generate data at the edge. Understand their capabilities, data generation methods, and integration techniques.
- Edge Nodes: Study the role of edge nodes in local data processing. Learn about their hardware specifications, processing capabilities, and deployment scenarios.
- Edge Servers: Understand the function of edge servers in storing and processing data locally. Familiarize yourself with different types of edge servers and their configurations.
- Edge Gateways: Learn how edge gateways manage data traffic between edge devices and servers. Understand their importance in ensuring efficient data flow and communication.
- Communication Networks: Study the various communication networks that connect edge devices, nodes, and servers. Learn about network protocols, data transfer methods, and network topology.
Design Principles of Edge Architecture:
- Decentralization: Understand the importance of decentralizing processing tasks across multiple nodes. Learn how to design systems that avoid single points of failure.
- Scalability: Study how to design scalable edge architectures. Learn about techniques to handle increasing data volumes and the addition of new devices.
- Interoperability: Learn how to ensure interoperability among diverse devices and communication protocols. Study standards and best practices for seamless integration.
- Resilience: Understand the principles of designing resilient edge systems. Learn how to achieve high availability and fault tolerance.
- Security: Study the security considerations specific to edge computing. Learn about data encryption, access control, and anomaly detection.
Benefits of Edge Architecture
Here are the key benefits of Edge architecture:
- Reduced Latency: Processing data locally reduces the time it takes for data to travel, resulting in faster response times. This is critical for applications such as autonomous vehicles and industrial automation, where real-time data processing is essential.
- Enhanced Security: Local data processing minimizes the risk of data breaches during transmission. Sensitive data remains within the local network, reducing exposure to potential cyber-attacks and enhancing overall security.
- Cost Efficiency: By processing data at the edge, organizations can reduce bandwidth costs. Less data needs to be transmitted to central servers, lowering the expenses associated with data transfer and storage in the cloud.
- Improved Reliability: Edge architecture ensures continuous operation even when network connectivity is intermittent. Local processing allows critical applications to function without relying on a constant connection to central servers.
- Scalability: Edge architecture can easily scale to accommodate more devices and increased data volumes. New edge nodes can be added as needed, without overwhelming the central infrastructure.
Use Cases and Applications of Edge Architecture
Here are the key use cases and applications of edge architecture:
- Healthcare: Edge computing supports real-time monitoring and analysis of patient data through wearable devices and sensors. This allows for immediate medical interventions and continuous health monitoring without relying on cloud connectivity.
- Manufacturing: In smart factories, edge computing enables predictive maintenance and real-time quality control. By analyzing data from sensors on the production line, manufacturers can detect issues early and reduce downtime.
- Smart Cities: Edge architecture helps manage urban infrastructure efficiently. Traffic management systems use local data to optimize signal timings and reduce congestion. Similarly, smart grids leverage edge computing for efficient energy distribution and monitoring.
- Retail: Retailers use edge computing for personalized shopping experiences and efficient inventory management. In-store sensors track customer behavior and preferences, enabling targeted promotions and optimized stock levels.
- Autonomous Vehicles: Edge computing is crucial for the operation of autonomous vehicles. It processes data from various sensors and cameras in real-time, ensuring safe navigation and quick response to environmental changes.
- Agriculture: Edge devices in agriculture monitor soil conditions, weather, and crop health. Farmers receive real-time insights and can make informed decisions to enhance crop yield and reduce resource wastage.
Challenges and Solutions of Edge Architecture
Implementing edge architecture comes with its own set of challenges. These challenges need to be addressed to ensure the effective functioning of edge systems. Here are the key challenges and their solutions:
- Data Management: Managing large volumes of data locally can be complex and resource-intensive.
- Solution: Implement robust data management frameworks and local storage solutions. Use data compression and efficient data handling techniques to optimize storage and processing.
- Interoperability: Integrating diverse devices and communication protocols can be difficult.
- Solution: Adopt standardized communication protocols and interoperability frameworks. Ensure that all edge devices can communicate seamlessly with each other and with central systems.
- Scalability: Ensuring that edge architecture can scale with growing data volumes and devices.
- Solution: Design scalable edge infrastructure that can handle increased data loads. Use modular and flexible systems that can be easily expanded as needed.
- Latency: While edge computing reduces latency, some applications require extremely low latency that can be hard to achieve.
- Solution: Optimize network infrastructure and use high-speed communication channels. Implement edge nodes strategically to minimize data travel distance.
- Security: Protecting distributed data from cyber threats is a major concern.
- Solution: Implement strong encryption for data at rest and in transit. Use advanced authentication and access control mechanisms to secure edge devices and networks.
- Maintenance: Regular maintenance of numerous edge devices can be challenging and costly.
- Solution: Develop automated maintenance and monitoring systems. Use predictive maintenance techniques to identify potential issues before they occur.
Security Considerations for Edge Architecture
Security is a critical aspect of edge architecture due to its decentralized nature. Protecting data across multiple edge devices and nodes requires a comprehensive security strategy. Here are the primary security considerations and measures for edge architecture:
- Data Encryption: Protect data both at rest and in transit to prevent unauthorized access.
- Solution: Use robust encryption protocols like AES for data at rest. Implement TLS or IPSec for data in transit to ensure secure communication between edge devices and servers.
- Authentication and Access Control: Ensuring only authorized users and devices can access the system.
- Solution: Implement multi-factor authentication (MFA) to verify user identities. Use role-based access control (RBAC) to manage permissions and restrict access based on user roles.
- Device Security: Protecting edge devices from physical and cyber threats.
- Solution: Deploy tamper-resistant hardware and secure boot processes. Regularly update device firmware to patch vulnerabilities and enhance security.
- Network Security: Securing the communication channels between edge devices and central servers.
- Solution: Use network segmentation to isolate sensitive data and limit potential breaches. Deploy intrusion detection and prevention systems (IDPS) to monitor and block malicious activities.
- Anomaly Detection: Identifying and responding to unusual activities in real-time.
- Solution: Implement AI and machine learning algorithms to detect anomalies. Use automated response systems to quickly address potential security threats.
Comparison with Cloud and Other Architectures
Edge architecture offers distinct advantages over traditional cloud and other computing architectures. Understanding these differences helps in selecting the right approach for specific applications. Here are the key comparisons:
- Latency: Edge computing processes data locally, reducing latency significantly.
- Cloud Computing: Data must travel to centralized servers, increasing latency. This can be problematic for applications requiring real-time processing.
- Fog Computing: Sits between edge and cloud, reducing latency but not as effectively as pure edge computing.
- Bandwidth Usage: Edge computing reduces the need to transfer large volumes of data over the network.
- Cloud Computing: Requires substantial bandwidth to transfer data to and from central servers. This can lead to high operational costs and potential bottlenecks.
- Fog Computing: Reduces bandwidth usage compared to cloud computing but still requires significant data transfer.
- Data Security: Edge computing enhances security by processing data locally.
- Cloud Computing: Involves transmitting data over the internet, which can expose it to security risks. Cloud providers must implement robust security measures to protect data.
- Fog Computing: Offers improved security over cloud computing but still relies on data transfer through the network.
- Scalability: Edge architecture supports scalable solutions by distributing processing tasks.
- Cloud Computing: Highly scalable due to centralized resources, but can be expensive for large-scale deployments. Scaling requires significant investment in infrastructure.
- Fog Computing: Offers moderate scalability, balancing between edge and cloud.
- Operational Costs: Edge computing can lower operational costs by reducing data transfer and cloud storage needs.
- Cloud Computing: Operational costs can be high due to data transfer and storage fees. While cloud services offer flexibility, costs can escalate with increased usage.
- Fog Computing: Moderate operational costs, offering a balance between edge and cloud costs.
Conclusion
Edge architecture brings data processing closer to the source, reducing latency and enhancing security. It offers significant benefits for real-time applications across various industries. Despite challenges, effective solutions ensure robust implementation. Comparing edge with cloud and fog computing highlights its unique advantages. Understanding these differences helps in choosing the right architecture. Edge computing is crucial for efficient, secure, and scalable data processing.
|

