|
|
In IT Technologies, the companies are looking to bring the agileness in the software development workflow. To market and business their ideas into services to reach to their customers quicker and have competitive edge on the market. Because of this, Companies have shifting to DevOps culture to automated the workflow end to end completely with pipelines. Jenkins is the one of popular CI/CD pipeline tool and managing the security settings and acess controls are essential. In this article we will discuss on the effective management of jenkins security settings and access management controls. What Is Jenkins?Jenkins is an open-source automation server used for continuous integration and continuous delivery (CI/CD) in software development. Jenkins stand as a cornerstone tool for continuous integration and continuous delivery (CI/CD). However with all this features there might be some security threats that can occur in the deployment process. Managing Jenkins security settings and controlling access controls is critical to safeguard you pipelines , repository and sensitive data for your deployement. Jenkins has project based security and access control for its repository to control who can use and edit a repo data. Jenkins also has user logging feature to track user action , configuration changes and system events. Audit log helps to review security-related activities. Need For Security In JenkinsSecurity in Jenkins is important for safeguarding sensitive data, including source code, credentials, and deployment configurations , against any misuse. Protection against malware, cyberattack is maintained through access control, encryption, and regular security updates. Moreover Jenkins upholds the data confidentiality and privacy , securing personally identifiable information(PII) processed during build and deployment processes. By adding security , Jenkins security measures contribute and maintaining business continuity , minimizing disruption , and safeguarding against financial loss. Understanding Of Primary Terminologies
Managing Security Settings And Access Controls In Jenkins: A Step-By-Step GuideStep 1: Access Jenkins Dashboard
http://{IP_Address}:8080
Step 2: Install Required Plugins
Step 3: Accessing Jenkins Security Settings
Step 4: Configure Your Authentication Model
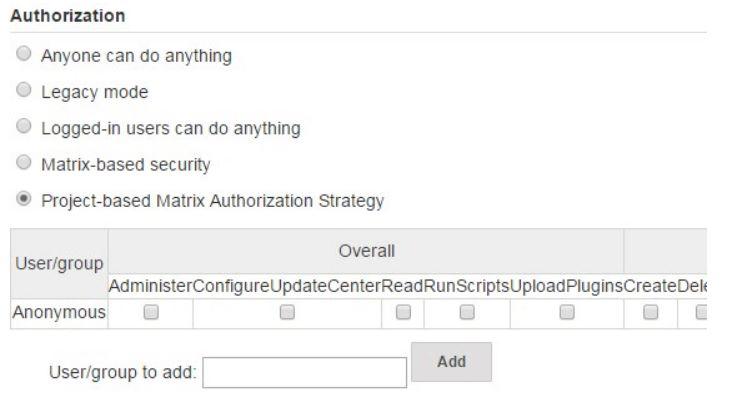
Step 5: Setting Authorization
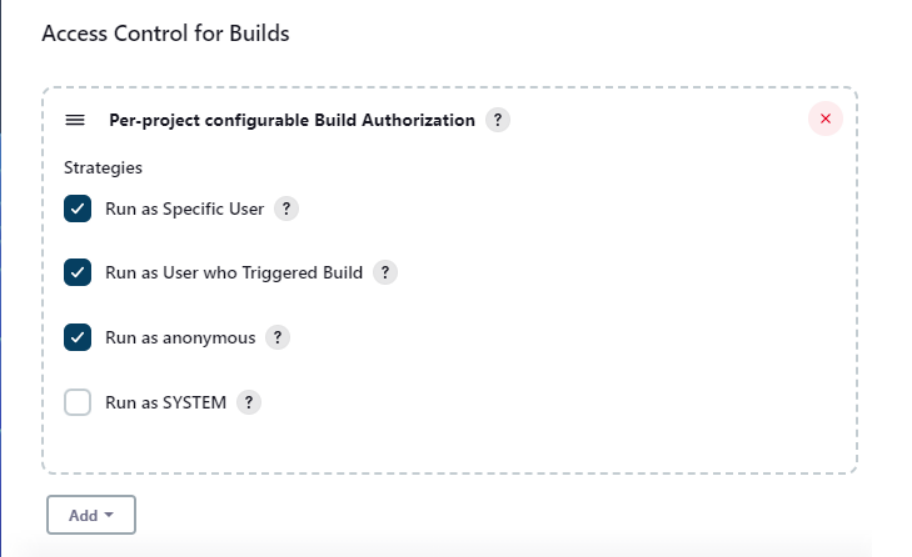
Step 6: Securing Indivdual project
ConclusionSecuring your Jenkins is very important for your CI/CD pipeline and sensitive data. By understanding and implementing security settings and access control, you can mitigate any potential risk and ensure the integrity and confidentiality of your Jenkins environment. Through this article we have taken you through the knowledge to navigate jenkins security settings and controlling access permissions in Jenkins. Managing Security And Access In Jenkins – FAQ’sHow Can I Recover Access If I Lock Myself Out Of Jenkins?
Can I Enforce Multi-factor Authentication (MFA) In Jenkins For Added Security?
How Can I Restrict Access To Certain Plugins Or Administrative Features?
Can I Integrate Jenkins With External Identity Providers Like LDAP?
|
Reffered: https://www.geeksforgeeks.org
| DevOps |
Type: | Geek |
Category: | Coding |
Sub Category: | Tutorial |
Uploaded by: | Admin |
Views: | 14 |