|
|
In this article, we will see the Preventing Common Vulnerabilities in JavaScript. Before we proceed, we will first understand the list of most common Vulnerability attacks, & then will understand the various approaches to resolve those Vulnerability attacks. Finally, we will understand the concept with the help of basic illustrations. Table of Content List of Common VulnerabilitiesThe following is the list of the most common Vulnerabilities:
List of Preventive Approaches
Cross-Site Scripting (XSS) PreventionThe XSS occurs when an attacker injects malicious scripts into a web application which are then executed in a user’s browser. This can lead to stealing sensitive data or compromising user sessions. The preventive approach is to Sanitize user inputs and escape output using the appropriate encoding functions. A detailed description of prevention is covered in Cross Site Scripting (XSS) Prevention Techniques article. Example: This example illustrates the prevention from Cross-Site Scripting (XSS) in JavaScript. HTML
Output: 
Cross-Site Request Forgery (CSRF)The CSRF involves tricking a user into performing unwanted actions without their consent and This happens when an attacker uses a user’s authenticated session to perform the actions on a different site. The preventive approach is to implement CSRF tokens in forms to validate the authenticity of the requests. Use SameSite cookies to restrict cookies from being sent in the cross-origin requests. Please refer to the Cross-Site Request Forgery (CSRF) Protection Methods and Bypasses Article for a detailed description. Example: This example illustrates the basic implementation of the Cross-Site Request Forgery (CSRF). HTML
Output: 
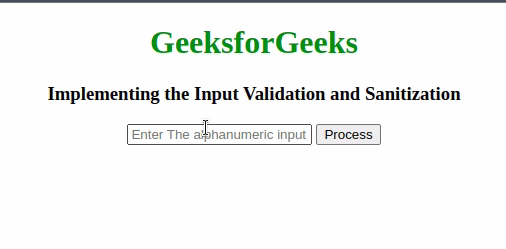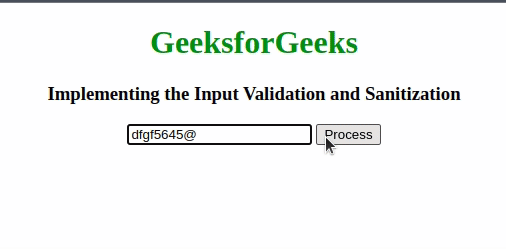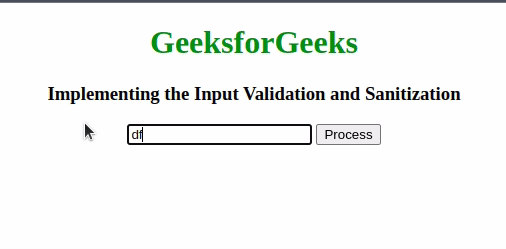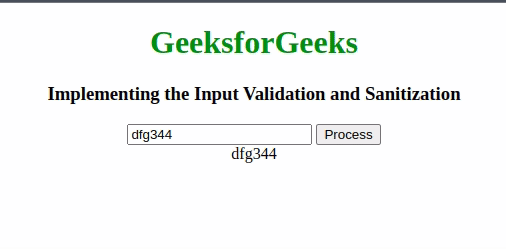
Input Validation and SanitizationIn this approach, we’ll be using Regular Expressions to validate and sanitize input. Regular Expression has a sequence of characters that forms a search pattern. The search pattern can be used for text search and text to replace operations. In the case of Sanitization, it takes the help npm package that can be used to sanitize file names by removing all the unwanted characters or white spaces from the file name and making it a proper file name according to the specific file system or operating system. Example: This example illustrates the basic implementation of Input Validation and Sanitization. HTML
Output:
ConclusionSecuring JavaScript applications is paramount to prevent common vulnerabilities and Cross-site scripting (XSS) cross-site request forgery (CSRF) inadequate input validation and other vulnerabilities can have serious consequences. By implementing proper sanitization input validation using the security tokens and following secure coding practices developers can significantly reduce the risk of their applications being exploited. |
Reffered: https://www.geeksforgeeks.org
| JavaScript |
Type: | Geek |
Category: | Coding |
Sub Category: | Tutorial |
Uploaded by: | Admin |
Views: | 13 |