|
In distributed computing, consensus protocols are crucial for coordinating processes and ensuring system reliability. Among these protocols, the Ring and Bully algorithms are prominent examples, each designed to elect a leader or coordinator within a network of interconnected nodes. Understanding the differences between these two algorithms is essential for grasping their respective advantages and applications in distributed systems.
 Ring vs. Bully Algorithm
Important Topics for Ring vs. Bully Algorithm
Election Algorithms have two assumptions such as:
- Each process that is involved has a unique identification number.
- Each process knows the identification number of every other process.
What is the Ring Algorithm?
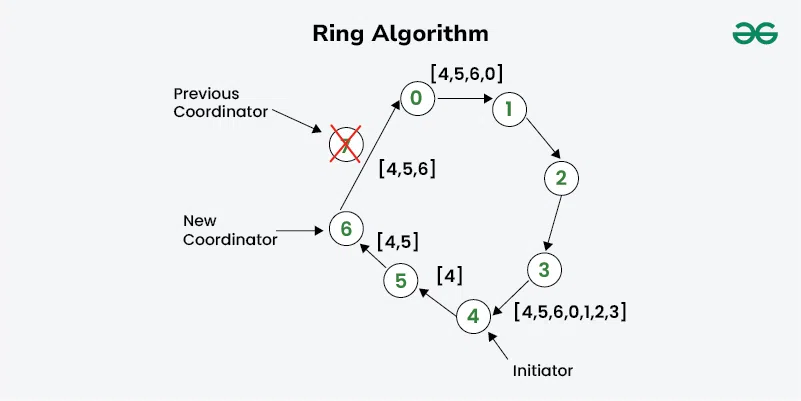
Ring Algorithm starts its process of selecting of coordinator once any process connected in the ring notices that the coordinator is not functioning. The initiating process then prepares an election message that contains its own process number and then sends this message to its successor in the ring. If the successor is not functioning then it kills that successor and sends it to the next one.
- Every next process then adds its process number to the message and delivers the message to the next process connected in the ring.
- It continues until the message again reaches the initiating process.
- Now the message consists of the process number of all the functioning processes.
- The process that has the highest ID wins the election. The initiating process then sends another message in the ring about the winning process.
 Ring Algorithm What is the Bully Algorithm?
Bully Algorithm starts its process of selecting of coordinator when a working process notices that the coordinator is not responding to it and then initiates an election. The selection of a coordinator sends an election message to all the other available processes.
- If none of the process responds to its message the process itself wins the election and becomes the coordinator.
- Meanwhile, if any process that has a higher ID than the initiating process answers, it takes charge of initiating the process.
- In this algorithm, the bully guy that is the participating process that has the highest ID becomes the coordinator. This approach is efficient in terms of fault tolerance but complex to implement.
Difference between Ring and Bully Algorithm
Below are the differences between Ring and Bully Algorithm:
|
Parameter
|
Ring Algorithm
|
Bully Algorithm
|
|
Communication Strategy
|
In a ring algorithm communication between the processes takes place in the logical ring structure.
|
In the bully algorithm, direct communication takes place between all the processes.
|
|
Process of Election
|
The process of election takes place by passing a message along the ring.
|
The process of election takes place by directly messaging the processes with higher process ID
|
|
Selection of new Coordinator
|
In the ring algorithm, the process that has the highest ID in the ring becomes the new Coordinator.
|
In the bully algorithm, the process that has the highest ID among the responding processes becomes the new Coordinator
|
|
Response Mechanism
|
In the ring algorithm, the message is being forwarded or it responds with a higher ID.
|
In the bully algorithm, one process responds to another by sending an “OK” message
|
|
Complexity
|
The ring algorithm is less complex.
|
The bully algorithm is more complex than the ring algorithm.
|
|
Scalability
|
The ring algorithm is more scalable when the number of processes is small.
|
The bully algorithm can work well when the number of processes is more.
|
|
Fault Tolerance
|
The ring algorithm can be affected when the ring is broken. As there will be no complete message passing and communication between the processes.
|
The bully algorithm can handle such faults as the communication takes place directly between two different available processes
|
|
Utilization of Resources
|
The ring algorithm requires fewer resources for communication because the messages are being shared among the processes connected in the ring.
|
Bully Algorithm increases the communication overhead because the messages are being sent directly from one process to another.
|
Use Cases of Ring Algorithm
The Ring algorithm is commonly used in scenarios where nodes are organized in a logical ring topology. Below are some specific use cases:
- Token Passing Systems:
- In systems where nodes need to pass a token around a ring to ensure fair access or to enforce a sequence of actions, the Ring algorithm can be employed.
- For example, in networks where only the node holding the token can perform certain critical operations or access shared resources, the Ring algorithm helps in maintaining orderly access.
- Message Routing:
- In distributed systems where messages or tasks need to be routed sequentially through each node in a ring structure, the Ring algorithm ensures that each node receives and processes the message in a predefined order.
- This can be useful in load balancing tasks or in implementing distributed algorithms where each node performs a part of a larger computation.
- Leader Election:
- Although the Bully algorithm is more commonly associated with leader election, the Ring algorithm can also be adapted for scenarios where a leader needs to be elected among nodes in a ring topology.
- Each node in the ring can participate in the election process, with messages passed around the ring until a leader is determined based on a predefined criteria.
Use Cases of Bully Algorithm
The Bully algorithm is particularly suited for scenarios where nodes are organized in a decentralized fashion and a leader needs to be elected or re-elected reliably. Below are its primary use cases:
- Leader Election:
- This is the most common use case for the Bully algorithm. In distributed systems, it ensures that if the current leader fails or becomes unavailable, a new leader can be elected seamlessly.
- Nodes initiate an election process to select a new leader, ensuring that the elected leader is the highest priority node among those participating.
- Fault Tolerance:
- The Bully algorithm enhances fault tolerance by ensuring there is always a leader node capable of making decisions or coordinating actions.
- This is crucial in systems where uninterrupted operation is required despite the failure of individual nodes.
- Resource Management:
- In systems where nodes compete for resources or where a single node needs to coordinate resource allocation or task distribution, the Bully algorithm can be used to elect a coordinator that manages these responsibilities efficiently.
Conclusion
Election Algorithms such as ring and Bully algorithm plays a very vital role while selecting a coordinating process among all the available processes. This coordinator process is responsible for the proper functioning and execution of the operation. Comparing both the Algorithms the approaches are different but the ring algorithm is less complex as compared to the bully algorithm whereas the bully algorithm is efficient for fault tolerance as the communication takes place from one process to another.
|


