
|
|
SSH is short for Secure Shell or Secure Socket shell. According to Wikipedia, the Secure Shell Protocol is a cryptographic network protocol for operating network services securely over an unsecured network. sshd is short for Secure shell daemon. SSH is one of the most reliable ways that you can choose to secure your Linux server-Virtual Private Server, which may be hosted on the Cloud or a server that you have hosted locally on your machine. This article assumes that you already have ssh utilities installed on your Linux machine. Configuration and Security OptionsStep 1: Generate ssh key pairs using the keygen utility.Open your Linux terminal and connect to your server. Next on the client side(open another terminal) run the following commands to log in using ssh key pairs. To generate public and private key pairs execute the below command:

To view, the id_rsa.pub key, then run execute the below command. cat .ssh/id_rsa.pub 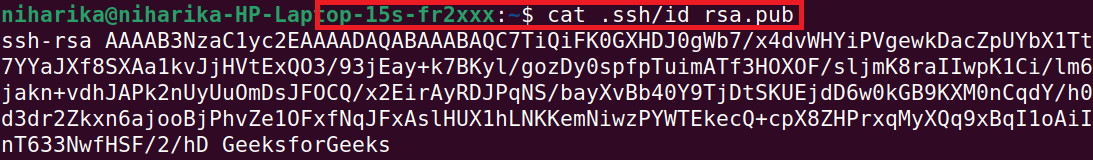
The below command lists the contents of the id_rsa file. cat.ssh/id_rsa 
Step 2: Now copy the keys to your virtual machineRun the below command on your machine to copy the keys. ssh-copy-id {username}@{ipaddress}
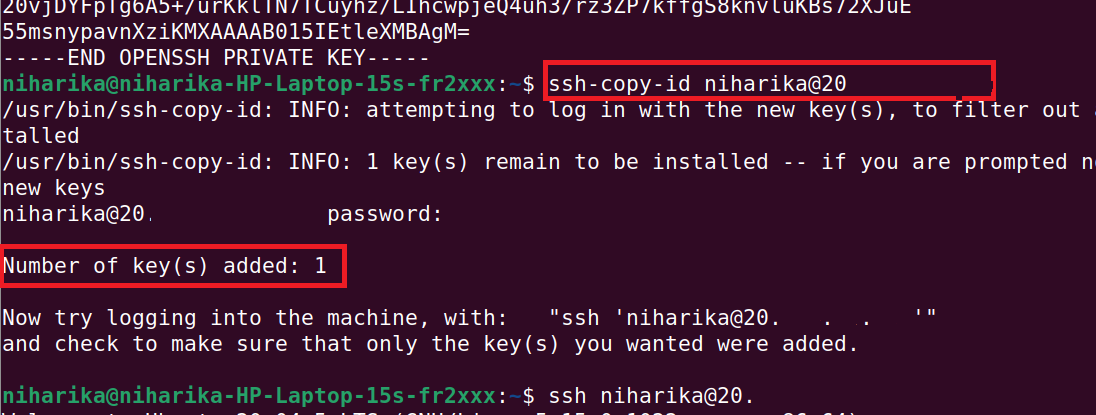
Step 3: If you want to disable password authentication, open sshd configuration by running(It is recommended)sudo vim /etc/ssh/sshd_config Look for the PasswordAuthentication option and change it to no 
Remove the “#” symbol before the PasswordAuthentication (or any option that you wish to modify) and change it to no. Make sure that the PubkeyAuthentication is set to yes The authorized keys file shows all the keys that you have generated. Now restart the ssh service by running the below command: systemctl restart ssh When you open the sshd configuration, you will notice many options there. We will discuss some of them here. 
Option 1: Port 22 The port by default is set to 22. If you wish to change the default settings, remove the comments and enter a port of your choice. It is recommended that you do not use port 22 as anyone trying the infiltrate your system is most likely to check port 22 for vulnerabilities first.  changing port number Option 2: AddressFamily This allows you to configure the type of addresses you want to connect to your server like ssh, bastion(for linux machine hosted virtually on Microsoft Azure), ipv4, ipv6, etc. The default is ‘Any’ which allows you to connect to your server using any protocol. Option 3: MaxAuthTries This allows you to set the maximum limit to wrong password entries. It is essential because it helps to protect your server against possible brute-force attacks. 
Option 4: MaxSessions This option allows you to enter a limit on the number of sessions that a user can have active. Just in case the user ever leaks their passwords, this option provides additional security.  Max Auth Tries and Max Sessions- changing the defaults Option 5: Choosing your desired algorithm The default algorithm for public and private keys is the RSA algorithm. However, you can change the type of the algorithm to suit your needs using the following key generation command:

|
Reffered: https://www.geeksforgeeks.org
| Linux Unix |
Type: | Geek |
Category: | Coding |
Sub Category: | Tutorial |
Uploaded by: | Admin |
Views: | 12 |