|
|
When it comes to working in the digital world, the question of files’ authenticity is of great importance. A checksum is data computed from data contained in the given file which can be used to check if the given file was modified or not. This article will help you how to find the checksum of a file and whether it is correct or not using Get-FileHash in Powershell in Windows. What is Hash?Hash is an alphanumeric string created by processing bytes of the file by some algorithm. This hash value is of significantly lower magnitude than the size of the actual file and is listed right alongside the file that you are downloading; allowing you to take your downloaded file, run your hash value against it, and check if the two hashes match. The use of these hashmap values is different algorithms and utilities that are used that come with the programming languages. Every algorithm will provide another hash; however, the utility used for creating the hash will provide the same hash value when you select another algorithm. What is a Checksum?A checksum is a value created from the data within a file. This has the role of pointing at the file like a fingerprint. When a file is downloaded one can hash it and compare it to the checksum of the file given by the source to check if the file was modified. Why Verify Checksums?
Using Get-FileHash in PowerShellPowerShell is a scripting language and command-line interface to the operating system for administration. Get-FileHash is a cmdlet that calculates the hash value for a file using a named hash algorithm. Step 1: Open PowerShellPress Windows + X and select Windows PowerShell (or Windows PowerShell (Admin) if you need administrative privileges). Step 2: Navigate to the File DirectoryUse the cd (Change Directory) command to navigate to the directory where your file is located. For example, if your file is in C:\Users\YourName\Downloads, you would enter: cd C:\Users\YourName\Downloads
Step 3: Calculate the File’s ChecksumTo calculate the checksum of the file the Get-FileHash cmdlet needs to be run and the file path needs to be supplied. Indeed, by default, the hash of the image is calculated using the SHA-256 algorithm, but you can set what kind of hash to generate, for instance, MD5 or SHA-1. For SHA-256:Get-FileHash yourfile.ext
For MD5:Get-FileHash yourfile.ext -Algorithm MD5
For SHA-1:Get-FileHash yourfile.ext -Algorithm SHA1
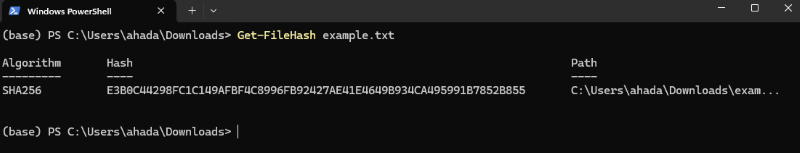
Replace yourfile.ext with the actual name and extension of your file. Example:If you have a file named example.txt in the current directory: Get-FileHash example.txt
The output will look something like this: Algorithm Hash Path  Hash Code Output Step 4: Compare the ChecksumCompare the computed checksum with one that is given by the source. If they match, congratulations, your file is still safe. Otherwise, the file could be accidentally corrupted or modified in some way and the original lost. (Get-FileHash C:\Users\YourName\Downloads\example.txt -A SHA256).hash -eq "YourHashCode"
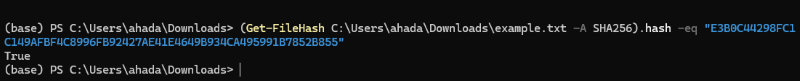 Comparing The Output results as True, Its matched. Detailed Explanation1. Opening PowerShell:
2. Navigating to the File Directory:
3. Calculating the File’s Checksum:
4. Comparing the Checksum:
Common Hash Algorithms
Here are a few items to be aware of:
As mentioned above you can write some text in a file and use such a file as the location of a variable in Go, and in the same time get the same hash value. Hashes are calculated on the content to check their authenticity. You can try for instance, modifying the text from “Hello World” to “Hello world”(lowercase w on “world) Here, you will note that the hash that is generated is different. LARGE FILESIn addition to simple checks when comparing the content, adjusted for the fact that downloaded files can be larger, a hash is useful when there are large copies. For instance, just the other day I was working on a file transfer of a relatively big size where there was a rude interruption from the network. The transfer auto-resumed, but due to this network interruption I could not be certain there was no data corruption. I reverted the hash on both the source and the destination to check if there were any problems with the file; as a result, I saved an hour of downloading a file that did not need to be downloaded again. VALIDATE AGAINST TAMPERINGAnother use of this could be to perhaps guarantee that files were not altered. Of course, you can have good security measures in place, but there is always a way that someone can reach files that they should not. If you want to be sure files were not touched at all, you can record the result of computation against all the files into a text file and put that into another location/into immutable media. And then any time you need to do validation, you can run another compute against those files and invariably, all is well. This will nicely suit the paranoid person within your organization to the extreme. ConclusionChecksum is an effective and very basic way of confirming that the content you are receiving or the physical storage media is indeed secure and has not been tampered with. By conducting this in PowerShell, the task is easy and quick because the Get-FileHash cmdlet can accomplish this. Thus, using the tips described in this article, you can effectively check the reliability of the files in Windows. NOTE: Ensure that you always compare the checksum provided by the file source to detect any potential tampering or corruption. This practice is crucial for maintaining the security and reliability of your digital files. How to Verify Checksum of a file in Windows – FAQsWhy is verifying a checksum important?
How do I verify a checksum?
What should I do if the checksums don’t match?
|
Reffered: https://www.geeksforgeeks.org
| TechTips |
Type: | Geek |
Category: | Coding |
Sub Category: | Tutorial |
Uploaded by: | Admin |
Views: | 24 |