|
The Bully Algorithm is an important method in distributed systems, facilitating leader election among nodes. It ensures continuity by autonomously electing a new leader when the current one fails, crucial for maintaining system coordination and resilience.
 Bully Algorithm in Distributed System Important Topics for Bully Algorithm in Distributed System
What is the Leader Election Algorithm?Leader election is a critical process in distributed systems where nodes (computers or processes) must elect a leader among themselves. The leader often assumes responsibilities such as coordination, resource allocation, or decision-making on behalf of the group. Ensures that there is always a designated node responsible for managing tasks or resources, even in dynamic environments where nodes can fail or join.
The election algorithm is based on the following assumptions:
- Each process has a unique priority number.
- All processes in the system are fully connected.
- The process with the highest priority number will be elected as coordinator.
- Each process knows the process number of all other processes.
- What the process doesn’t know is which process is up or down.
- During recovery, the failed process can take appropriate steps to resume the set of active processes.
Note: The goal of the election algorithm is to ensure the following factors:
- There should be only one leader among the processes.
- All Processes agree on who is the leader.
We have two election algorithms for two different configurations of a distributed system.
- Bully Algorithm
- Ring Algorithm
What is the Bully Algorithm for Leader Node Election?The Bully Algorithm is a well-known leader election algorithm used in distributed systems that operates on the principle of higher priority. Here’s how it works:
- Initiation: When a node detects that the current leader has failed (usually through a timeout mechanism), it initiates an election.
- Election Process:
- The initiating node sends an “election” message to all other nodes with higher priority.
- Nodes with higher priority respond by either acknowledging their current leader status or declaring themselves candidates.
- If no higher-priority node responds, the initiating node assumes leadership.
- Notification: The newly elected leader informs all nodes of its leadership status, ensuring consistency across the distributed system.
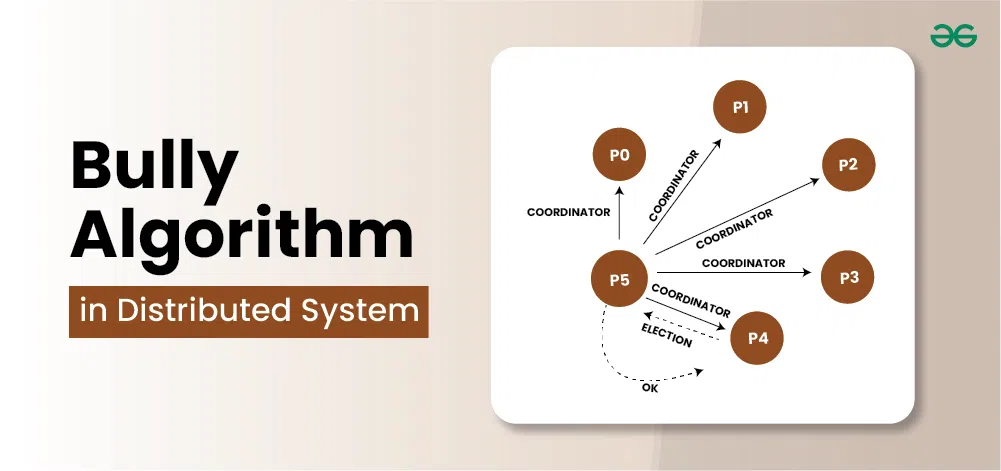
Messages in Bully Algorithm for Leader Node ElectionThere can be three types of messages that processes exchange with each other in the bully algorithm:
- Election message: Sent to announce election.
- OK (Alive) message: Responds to the Election message.
- Coordinator (Victory) message: Sent by winner of the election to announce the new coordinator.
Steps Involved in Bully Algorithm for Leader Node ElectionLets understand the steps involved in bully algorithm for leader Node Election through an example. The example follows all the assumptions discussed above in the Election Algorithm. Let’s say there are 6 Processes P0, P1, P2, P3, P4, P5 written in ascending order of their Process ID (i.e.,0, 1,2,3,4,5).
Bully Algorithm Code in Java Below is the code of bully algorithm in java:
Java
import java.util.ArrayList;
import java.util.List;
// Class representing a node in the distributed system
class Node {
private int nodeId;
private boolean isCoordinator;
public Node(int nodeId) {
this.nodeId = nodeId;
this.isCoordinator = false;
}
public int getNodeId() {
return nodeId;
}
public boolean isCoordinator() {
return isCoordinator;
}
public void setCoordinator(boolean coordinator) {
isCoordinator = coordinator;
}
// Method to initiate an election
public void initiateElection(List<Node> nodes) {
System.out.println("Node " + nodeId + " initiates election.");
for (Node node : nodes) {
if (node.getNodeId() > this.nodeId) {
// Send election message to higher priority nodes
node.receiveElectionMessage(this);
}
}
// Assume election process completes after initiating
becomeCoordinator();
}
// Method to receive election message from another node
public void receiveElectionMessage(Node sender) {
System.out.println("Node " + nodeId + " receives election message from Node " + sender.getNodeId());
// Respond if current node has higher priority
if (this.nodeId > sender.getNodeId()) {
System.out.println("Node " + nodeId + " responds to Node " + sender.getNodeId());
sender.receiveResponse(this);
}
}
// Method to receive response and acknowledge as coordinator
public void receiveResponse(Node sender) {
System.out.println("Node " + nodeId + " receives response from Node " + sender.getNodeId());
}
// Method to become the coordinator
public void becomeCoordinator() {
System.out.println("Node " + nodeId + " becomes the coordinator.");
this.isCoordinator = true;
}
}
public class BullyAlgorithmExample {
public static void main(String[] args) {
// Create nodes
Node node1 = new Node(1);
Node node2 = new Node(2);
Node node3 = new Node(3);
Node node4 = new Node(4);
Node node5 = new Node(5);
// List of nodes in the distributed system
List<Node> nodes = new ArrayList<>();
nodes.add(node1);
nodes.add(node2);
nodes.add(node3);
nodes.add(node4);
nodes.add(node5);
// Simulate failure of current coordinator (Node 3)
node3.setCoordinator(false);
// Assume Node 3 detects coordinator failure and initiates election
node3.initiateElection(nodes);
}
}
Explanation of the Code:- Node Class: Represents each node in the distributed system with attributes
nodeId and isCoordinator. It includes methods for initiating an election (initiateElection), receiving election messages (receiveElectionMessage), handling responses (receiveResponse), and becoming the coordinator (becomeCoordinator). - BullyAlgorithmExample Class: Contains the
main method where nodes are created (node1 to node5). Nodes are added to a list (nodes) representing the distributed system. In this example, node3 initiates an election due to a simulated failure of the current coordinator (node3 itself). - Output: When you run this code, it will simulate the election process and print messages indicating election initiation, message exchange, and the election outcome where a new coordinator node is elected based on their IDs.
This implementation is simplified and assumes a basic scenario. In practice, you would need to handle network communication, message exchange protocols, and potentially more complex failure scenarios to make the algorithm robust for real-world distributed systems.
Practical Applications of Bully Algorithm for Leader ElectionThe Bully Algorithm, despite its simplicity, finds practical applications in various distributed systems scenarios where leader election is crucial for maintaining system functionality and coordination. Here are some practical applications:
- Distributed Databases:
- In distributed databases, nodes must agree on a leader to coordinate transactions, ensure data consistency, and handle queries efficiently. The Bully Algorithm can elect a node as the primary coordinator for managing database operations across multiple nodes.
- Fault Tolerance:
- The Bully Algorithm enhances fault tolerance by quickly detecting and replacing failed leader nodes. When a leader node becomes unresponsive due to a crash or network issue, the algorithm facilitates the election of a new leader, minimizing disruption and ensuring continuous operation of the distributed system.
- Decentralized Systems:
- In decentralized systems where nodes operate autonomously but occasionally need to synchronize or coordinate activities (e.g., peer-to-peer networks, IoT networks), the Bully Algorithm can elect a leader node responsible for controlling access, resource allocation, or data routing among peers.
- High Availability Architectures:
- Architectures designed for high availability rely on leader election algorithms like the Bully Algorithm to maintain redundancy and ensure that services remain accessible even if individual nodes or components fail. This is critical in cloud computing environments and mission-critical applications.
- Messaging Systems:
- In distributed messaging systems or event-driven architectures, the Bully Algorithm can designate a leader node responsible for managing message brokers, ensuring message delivery, and maintaining the consistency of event processing across distributed nodes.
Benefits of the Bully Algorithm for Leader ElectionBelow are the benefits of bully algorithm:
- Fault Tolerance:
- The Bully Algorithm enhances fault tolerance by quickly detecting when the current leader fails or becomes unresponsive. This triggers an election process to elect a new leader, ensuring continuous operation and resilience against node failures.
- Decentralized Nature:
- It operates in a decentralized manner, allowing nodes to autonomously initiate elections based on local observations (such as timeouts or failure detection). This reduces reliance on a central coordinator and distributes leadership responsibilities across the network.
- Simplicity and Efficiency:
- The algorithm is relatively simple to understand and implement, making it efficient for scenarios where a straightforward leader election mechanism is sufficient. It uses basic message passing and priority-based decision-making, which can be advantageous in environments where complexity needs to be minimized.
- Scalability:
- As the number of nodes in the distributed system increases, the Bully Algorithm scales well. Each node interacts with a subset of other nodes during the election process based on their priority, which helps manage scalability without overwhelming network resources.
Challenges of the Bully Algorithm for Leader ElectionBelow are the challenges of Bully Algorithm:
- Message Overhead:
- Nodes may need to exchange multiple messages during the election process, especially in larger networks or when nodes have similar priorities. This can introduce latency and increase network traffic, affecting overall system performance.
- Priority Assignment:
- Assigning priorities or identifiers to nodes in a fair and accurate manner is crucial. Incorrect or inconsistent priority assignments can lead to improper leader elections or instability in leadership transitions.
- Network Partitioning:
- During network partitions or transient connectivity issues, the Bully Algorithm may struggle to elect a leader or maintain consistency across all nodes. Nodes in isolated segments of the network may initiate separate elections, potentially leading to conflicting leadership claims.
- Handling Concurrent Elections:
- If multiple nodes detect a leader failure simultaneously or experience network delays, they may initiate concurrent elections. Managing these concurrent elections to ensure a single leader is elected and acknowledged by all nodes requires careful coordination and message handling.
FAQS for Bully Algorthm for Leader ElectionBelow are some faqs for bully algorithm for leader election:
Q1: How does the Bully Algorithm handle network partitions?The Bully Algorithm may face challenges during network partitions where nodes become isolated. Nodes in different partitions may initiate separate leader elections, potentially leading to inconsistent leadership claims. Strategies like timeout mechanisms and quorum-based decision-making can mitigate these issues.
Q2: What strategies can improve the efficiency of the Bully Algorithm in large-scale distributed systems?In large-scale systems, minimizing message overhead and ensuring timely election initiation and response handling are crucial. Techniques such as optimizing message exchange protocols, prioritizing nodes based on recent activity, or implementing distributed timers can enhance algorithm efficiency.
Q3: How does the Bully Algorithm ensure fair and consistent leader elections in environments with dynamically changing node priorities?Ensuring fair priority assignment and handling dynamic changes in node priorities require careful design. Algorithms may incorporate mechanisms for dynamically adjusting priorities based on node capabilities, workload, or system conditions to maintain fairness and consistency during elections.
Q4: What are the potential pitfalls or failure scenarios that the Bully Algorithm may encounter?Pitfalls include scenarios where multiple nodes detect a leader failure simultaneously, causing concurrent elections and potential inconsistency. Failures in message delivery or delayed responses can also impact the algorithm’s effectiveness, requiring robust error handling and recovery mechanisms.
Q5: How does the Bully Algorithm adapt to heterogeneous environments where nodes have varying processing capabilities or network conditions?Handling heterogeneity involves ensuring that all nodes can participate effectively in the election process, regardless of their capabilities or network constraints. Adaptive strategies may include adjusting timeout values, prioritizing nodes based on reliability metrics, or implementing adaptive message retry mechanisms.
ConclusionIn distributed systems, the Bully Algorithm is a simple and fault-tolerant leader election technique. It performs well in small- to medium-sized networks, maintaining order in the event of a leader failure. However, it lacks preemption capabilities and its efficiency can drop in larger networks.
|

